BLOG
Articles about website spoofing, cybersecurity trends, and how to protect your customers from hackers.
TRENDING: Fraudsters Abuse Dynamic DNS Subdomains for Phishing
Allure Security has observed an uptick in scammers using dynamic DNS (DDNS) services to claim subdomains on which they publish scam websites masquerading as known brands. In the examples we’ve seen, the phishing sites include brand logos and messaging as well as log-in fields.
Some DDNS providers allow users to create their own free subdomain on a public DNS server (e.g., fakesite.[DDNSprovider].net) that will then point to the IP address of their choice. Our AI-powered detection engine has recently flagged an increasing number of phishing websites that use subdomains created using dynamic DNS providers such as Duck DNS and ChangeIP.
Below we explain this trend observed by Allure Security’s threat response team, how fraudsters make use of the tactic, and tips for brands in mitigating this particular scheme.
Why do Dynamic DNS services exist?
Remotely accessing devices on your home network can be a hassle because the IP address for your home network changes regularly – in some cases daily. One of DDNS services’ legitimate use cases is facilitating remote access to devices on a home network. A DDNS service makes it easy to automatically map a domain name that doesn’t change to a regularly changing IP address like one for a camera on your home network.
DNS (Domain Name System) – sometimes referred to as “the phonebook of the Internet” – maps domain names to the IP addresses of servers on the Internet. If you type in “https://alluresecurity.dream.press” for example, DNS is the protocol that sends you to the correct IP address for our web server so that you can load our website.
Your router, which is the front door of your home network, has an IP address typically consisting of a string of at least 12 digits. Generally a consumer’s Internet service provider regularly changes the IP address of their customers’ routers.
Let’s say on your lunch break at work, you want to remotely connect to a camera at your home trained on your pet in its kennel to see what they’re up to. You might need the IP address of that camera in order to access it. Memorizing a single string of 12 or more digits is difficult, but it’s harder still when that number changes every day or week.
A hostname or URL such as maryspup.duckdns.org simplifies things. A DDNS service automates the regular updating of the mapping of the URL to the IP address so that your pet camera is accessible via your subdomain.
How do fraudsters abuse DDNS services?
Some DDNS providers such as DuckDNS, ChangeIP, and No-IP allow customers to create any custom subdomain they like for domains owned by the provider. Plus – many DDNS vendors also offer some level of their service for free. So, DDNS services offer a fraudster a free domain name, which they can point to a machine hosting a website anywhere in the world as long as it has an IP address.

Below we list examples of phishing sites that abused DDNS services, with subdomains redacted:
- [subdomain].duckdns.org/login.php (Duck DNS)
- [subdomain].lflinkup.org/ (Change IP)
- [subdomain].ns02.us/verify-uplink/Login/ (Change IP)
- [subdomain].serveuser.com/secure/ (Change IP)
- [subdomain].dns2.us/ (Change IP)
- [subdomain].dynamic-dns.net/ (Change IP)
DDNS can also help a scammer avoid detection for a longer period of time to extend a scam’s lifespan. If an organization’s online brand protection solution does not include subdomains in its data source, the scam may go undetected until a customer reports it.
You can’t find a deceptively named subdomain quite as easily as you can find a newly registered domain name for example. A newly registered domain name spreads across the DNS infrastructure by design and so is public knowledge that isn’t hard to come by (though of course there’s a humongous number of domain names registered each day).
Learning of a subdomain’s existence on the other hand is less obvious. Allure Security, for example, learns of them via three main sources among many:
- Passive DNS data is generated for example when someone attempts to visit a subdomain. This results in DNS queries, which are logged.
- Certificate transparency logs include information about certificates issued by Certificate Authorities and just like legitimate domain owners, fraudsters will request certificates for scam websites as well. You can monitor certificate transparency logs using tools such as Crt.sh or Meta’s Certificate Transparency Monitoring.
- Referrer logs tell you from what website a visitor arrived on your website. The last step in a scam after stealing a person’s data is usually to direct them to the official website in hopes not to tip the victim off to the fact that they were scammed.
Using DDNS and a subdomain also adds additional complexity to the take down process. A registrar won’t decommission an entire domain to address any one problematic subdomain. In the interest of privacy, many registrars will also refrain from providing you with contact information for their customers.
In that case, an impersonated brand will need to investigate to try and identify the host, which is not always straightforward. In addition, a subdomain is not always obviously using a domain provided by a dynamic DNS vendor (e.g., ChangeIP offers hundreds of domains for its free dynamic DNS services).
Each of these additional steps increases a scam’s lifespan. And when it comes to phishing, minutes count when every minute can result in more people falling victim.
Recommendations – What to do about online brand impersonation attacks that abuse dynamic DNS subdomains
Tips for brands
If an impersonation of your brand makes use of DDNS services, you will need to familiarize yourself with the DDNS providers’ terms-of-use/service and abuse policies (find abuse reporting information at the following links for Change-IP, DuckDNS, and No-IP).
In addition, consider the following:
- Ensure that looking at subdomains is part of your online brand impersonation monitoring regimen – Looking only at newly registered domains will miss the majority of attacks that use a subdomain from a DDNS provider
- Document impersonations – When you identify a brand impersonation, gather screenshots of the offending site and other evidence for your takedown request submission
- Get to know your data sources – Whether your online brand protection efforts are an in-house operation or something you hand over to a vendor, find out how you are monitoring for suspect subdomains (if at all). Are you monitoring passive DNS, certificate transparency data, DNS zone files? Do you mine your own web logs for referrers?
- Automate – Subscribing to a variety of feeds that might alert you to online brand impersonation attacks is not difficult (though you’ll quickly become overwhelmed by the volume and cost). Say you figure out how to get a feed of subdomains – there will be billions of them. How will you cull that list down to only those things that are relevant to your brand? There will still likely be too many of them for you or your team to manually eyeball. Effective online brand protection is becoming nearly impossible without automation.
- Evaluate the benefits of hiring an online brand protection expert like Allure Security – Online brand protection vendors have years of experience with playbooks for handling these sorts of issues and have built a reputation with many DDNS services to expedite takedown.
- BONUS TIP – Regularly review your DNS records – While not the topic of this article, using subdomain hijacking, attackers can take control of your subdomains and redirect them to malicious pages. This typically occurs when you’re no longer using a subdomain and you deleted the associated host, but did not remove the DNS record for that subdomain. Ensure you remove records for any subdomains you’re no longer using.
Tips for consumers
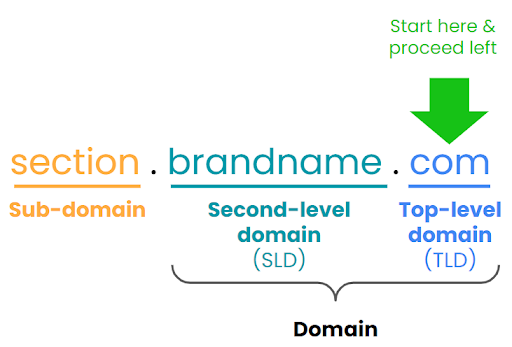
- Evaluate domains from the right to the left – Start with the top-level domain (e.g., .com, .org, .net, and thousands more). The domain name is directly to the left of the dot before the second-level domain. Anything to the left of the dot before the domain name is a sub-domain and should be scrutinized. For example, you shouldn’t trust the URL https://[financial institution].dns2.us.
- Use Google to investigate any questionable URL that uses a sub-domain – You may find that other people have already identified the URL as part of a scam. Or, you can enumerate the subdomains associated with a domain by using Google’s “site:” search function. Type “site:” into the Google search bar and the domain name (e.g., example.com) immediately after the colon as such: site:example.com., which will list the subdomains associated with that domain – however, know that this can be a long list of subdomains.
- If you encounter a fraudulent website, report it to the impersonated brand’s customer service team – whether you’ve fallen victim or not, reporting the fraudulent site to the brand can help in the effort to prevent others from falling victim.
What You Should Do Next
- Get the skinny on another recently rising brand impersonation attack trend we’ve observed – fraudsters embedding phishing pages in unrelated, compromised websites – on our blog.
- Compare your online brand protection efforts to modern online brand protection best practices using our free Busy Person’s Guide to Online Brand Protection.
- Find out how to streamline your monitoring of the internet for misuse of your brand on fake websites, deceptive social media profiles, and mobile app marketplaces by contacting us.
Posted by Sam Bakken