BLOG
Articles about website spoofing, cybersecurity trends, and how to protect your customers from hackers.
TRENDING: Fraudsters Embedding Credit Union Phishing Pages in Compromised Websites
Allure Security has observed an increase in scammers targeting credit union brands and their members by compromising vulnerable websites and adding pages impersonating credit unions to those sites via a subdirectory/subfolder. Some of these compromised sites contain multiple subdirectories/webpages impersonating multiple, unique credit union brands.
The imposter pages include a credit union’s logo, website content, and username and password fields used to steal banking credentials, as well as, links to fake account applications that steal identity information and payment details. Fraudsters use the stolen data to conduct identity, payment, and account takeover fraud.
This particular online brand impersonation attack tactic is not novel, but fraudsters using it against credit unions and their members is a recent growing trend. While attackers have targeted multiple vulnerable websites that use a number of different web hosting providers, we have seen these scams leveraging websites hosted by HostGator and hosting subsidiaries of Public Domain Registry. NOTE: This does not mean HostGator or Public Domain Registry is or is not inherently insecure, only that some compromised websites are hosted there.
Credit union leadership may need to re-evaluate their approach to detecting and responding to phishing sites targeting their brand because scammers likely use this method to evade detection based on permutations of domain names or monitoring newly registered domains.
How Fraudsters Use Compromised Websites to Steal Credit Union Members’ Credentials, Identities & Payment Information
Speculating on how attackers find and exploit these vulnerable websites in the first place is out of scope for this blog post. However, earlier this year a website consultant suggested that outdated, vulnerable WordPress plugins or weak passwords may be to blame.
Attackers can use automated scanning tools to find vulnerable WordPress sites and in some cases also automate the exploitation of those vulnerabilities in order to gain control of a website.
In another case last year, a GoDaddy WordPress data breach gave unauthorized parties access to users’ WordPress admin credentials allowing them to log in to these accounts and alter websites and their content.
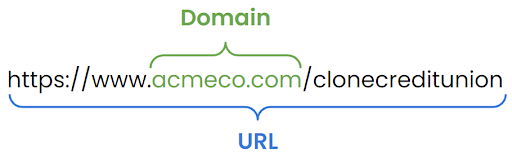
As illustrated above, a domain is what you might consider the main address of a website — acmeco.com in the image above. A subdirectory (also called a folder) organizes a website’s files within the domain and contains a page or pages — /clonecreditunion in the image above. In these cases, the domain is legitimate, but the URL taken as a whole is malicious.
Domains for compromised websites that we’ve observed include 0neverify, an IT services provider in India, the national government website of an island country in Africa, and more.
Sub-directories typically include an acronym for a credit union (i.e., Sam’s Credit Union abbreviated as /scu). In some cases we’ve also identified newly registered domain names redirecting to these malicious URLS. Some of these compromised websites have multiple sub-directories impersonating different credit unions similar to the following:
- https://[rootdomain].com/acu
- https://[rootdomain].com/zcu
- https://[rootdomain].com/yzcu
We also see a clear pattern in these online brand impersonation attacks leading us to believe:
- A single group may be responsible
- And/or tools that automate the creation of these phishing sites are for sale online making it easy for unskilled cybercriminals to execute such attacks
Similarities among the embedded credit union phishing pages include:
- Similarly structured, simple phishing pages
- Not direct clones of a legitimate site/page
- Use a credit union’s logo; basic username and password fields; and links for password recovery, account unlock, and account sign-up
- Same groups of hosting providers
What Credit Unions Need to Know About this Threat
Credit unions should pay attention to this trend to ensure their brand protection program covers as much ground as possible in hunting for fake websites targeting their members. For example, using a DNS permutation engine such as dnstwist alone to search for typosquatting (homoglyphs, omissions, subdomains, etc.) would not identify these phishing sites.
Similarly, because many of these domains have existed for a period of time, searching through feeds of newly registered domains alone would also fail to identify many of these online brand impersonations. The domain itself is “safe” while the page is malicious. So, intel and signals beyond those related to a domain name need to be collected and analyzed.
An important consideration in terms of responding to these impersonations is that response is not as simple as contacting the registrar or hosting company. A multi-pronged response is the most effective approach. For example, Allure Security mitigations of online brand impersonation attacks include blocklisting offending pages to prevent the majority of Internet users from accessing the site, inputting decoy data into log-in fields to disrupt the attacker’s financial model, and final clean-up including the removal of the page from the Internet altogether.
Takedowns for this sort of phishing page are far from simple. Sending an email to a registrar’s legal and abuse team will not suffice. Registrars will not or cannot simply take the entire domain offline because it hosts a fake login page. Nor can they usually take immediate action on it.
Response can require getting in touch with the hosting provider and website owner and having to explain to them what has happened. In many cases, depending on the website owner’s expertise, they will also need guidance on how to remove the offending content as well as taking care of the vulnerability to prevent recurrence of the scam. Working with an expert experienced in handling these particular threats shortens their lifespan and saves you time and money.
Recommendations – What Credit Unions & Members Can Do to Protect Themselves
For Credit Unions
- Ensure that in looking for impersonations of your brand online, you go beyond simply looking for permutations of your domain name – the majority of today’s attacks are designed to circumvent that approach
- If you don’t already, consider investing in an online brand protection service such as Allure Security’s in order to more effectively find and takedown scam sites before they do damage, as well as, save up to 88% compared to the costs of an internal brand protection function
For Credit Union Members
- Be sure to spend extra time inspecting the entirety of any URL you use to complete financial tasks online, especially on mobile devices
- Only use your credit union’s official app from the Apple App Store or Google Play or visit your credit union’s website only using the URL listed on the back of your payment card
- Avoid clicking on links sent to you via various digital communication channels such as e-mail, social media, SMS, etc.
- Report any suspicious or malicious communications purporting to come from your credit union to your credit union
For Owners of Compromised Websites
- Review these Hubspot tips for securing WordPress websites
- If you use HostGator to host your website, review HostGator’s tips for securing your website
What You Should Do Next
- Learn more about online brand protection and your options for protecting your organization’s brand online with our free Busy Person’s Guide to Online Brand Protection
- Download our Credit Union & Regional Bank Brands Under Attack report to learn more about the rising online brand impersonation threat
- If you’re ready to talk about your online brand impersonation detection and response program and how Allure Security can improve your effectiveness and reduce costs, contact us.
Posted by Sam Bakken

