BLOG
Articles about website spoofing, cybersecurity trends, and how to protect your customers from hackers.
Discover Your Cloud Data Loss Risk
Watch log activity, enrich logs with geolocation insights, score risks and inform data loss responses.
According to a recent ESG survey, companies are migrating data to the cloud faster than they can secure it. The research reveals 50% of survey respondents say they know that they have lost cloud resident data and 22% suspect they have lost data. The architect of this research, ESG Senior Analyst Doug Cahill, said, “The increased use of both sanctioned and unsanctioned cloud-based applications, in combination with security programs for the cloud that are often less mature than existing on-premise initiatives, has led to a significant loss of corporate data. Top contributors to data loss include violations of security policy, the misuse of access controls, and the implications of employees using their own devices.”
We help organizations understand Microsoft Office 365 use across organizations, and detect and respond to data loss resulting from stolen credentials, insider threats, malicious third parties, ransomware and human error.
Allure’s approach includes three main components:
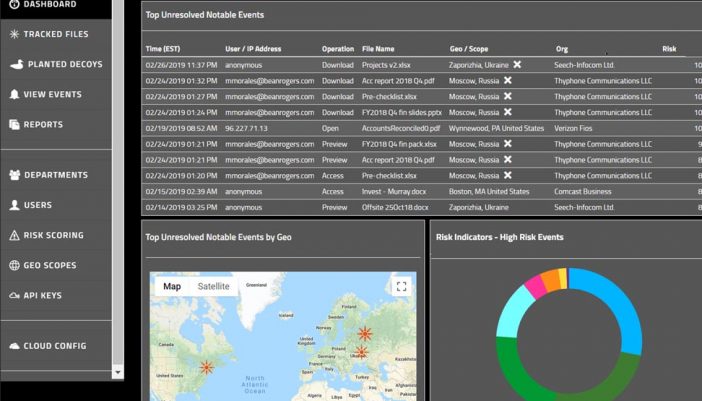
- Watch Office 365 file activity closely: See who interacts with which files, when and from where. Security teams can know in real time if bulk downloads occur, if files are accessed anonymously, and if documents are opened in risky locations or via unauthorized domains.
- Extend visibility beyond the cloud share: Agentlessly track activity even after documents are downloaded, copied or shared.
- Detect leaks and breaches: Know if insiders, malicious third parties, bots or hackers are snooping around confidential and sensitive files, and whether data is lost as a result. Also, security professionals can set up optional alerts to be informed when risky activity is in progress to inform response and limit data loss.
Our intuitive dashboard captures and visualizes risks so users can easily see noteable events with granular details and geolocation information, identify key indicators used to calculate and prioritize risks, and monitor most active users, domains, locations and operations. Additionally, users can drill down into specific document and user activity to collect forensics during active investigations.
“Allure’s detection and response capabilities intuitively bridge the collaboration benefits of Azure Information Protection (AIP), and provides valuable insights to Security Operations teams who are concerned about the confidentiality of their documents,” said Kartik Kanakasabesan,
– Azure Information Protection principal program manager.
Posted by Salvatore Stolfo